臺中市市立學校無線網路 Local Bridge Mode 服務
一、適用範圍
本市市立學校無線網路系統為 Aruba 無線基地台(Thin AP)且中央控制器
(controller)由教育局設備擔任。
二、建置目的
原無線系統提供 tc 及 tc-802.1x 兩 SSID,認證通過後因 IP 由教育局統一分
配,因此視同為校外使用者,無法取用校內的特定應用服務(如校內提供之印表
機、網路磁碟機、視訊教學..)。學校提出申請本項服務執行後,會以學校 tc-[Domain
Name] 新增 SSID,學校校內教職員生連線此 SSID 認證成功後,IP 將由校內提供,
故可取用校內限制使用的特定應用服務,提供校內教職員生進行校內行動學習之
需求。
臺中市市立學校無線網路 SSID 表列
SSID tc tc-802.1x tc-[學校 Domain] tc-[學校 Domain]-mac
無線協定 無 WPA2-Enterprise WPA2-Enterprise WPA2-PSK
加密方式 無 WPA2/AES WPA2/AES WPA2/AES
認證協定 Web 認證 802.1X
(PEAPv1/EAP-GTC)
802.1X
(PEAPv1/EAP-GTC)
MAC address
後端認證
主機 RADIUS Server LDAP Server
RADIUS/LDAP/AD
Server
RADIUS Server
使用對象
臨時訪客、跨區漫
遊、臺中市市立各級
學校教職員
臨時訪客、跨區漫
遊、臺中市市立各級
學校教職員
校內使用者 校內行動裝置
安控方式
校內網路無存取
權,僅提供上網服務
校內網路無存取
權,僅提供上網服務
可存取校內網路,並
提供上網服務
可存取校內網路,並
提供上網服務
三、學校端配合事項
1. 因認證成功後 IP 由校內提供,故建議學校在 Aruba AP 所在網段提供 DHCP
服務,方便行動裝置認證通過後自動取得 IP,進行網路存取。
2. 若學校規劃行動裝置取得 IP 為 Private IP,請學校端自行設置好 NAT 服務。
3. 因 IP 由校內提供,建議建置流量紀錄設備(Netflow、FortiAnalyzer..),
方便未來若發生資安事件之追踪。
4. 學校端 DHCP 服務可分配的 IP 數量請考量學校內同時連線的行動裝置數量。
四、服務方案
目前規畫下列 Local Bridge Mode 服務方案由學校自行考量後選擇合適方案進行建置,未提出申請之學校則維持現狀不改變。
方案 1. 登入所需帳號密碼認證由教育局提供及維護
帳號密碼為「教育局公務帳號」。
外校教職員生無法使用。
學校需至「教育局首頁」「7.公務作業」「7-1.公務作業專區」「7-1-2.
公務帳號管理」「單位人員管理」定期維護各校校內之人員名單。
方案 2. 登入所需帳號密碼認證由學校提供及維護
由學校全權決定哪些使用者可以使用無線網路 Local Bridge Mode 服務。
學校需提供認證服務 (RADIUS server、LDAP server 或 Windows AD)。
方案 3. 利用設備 MAC Address 認證
由學校全權決定哪些行動裝置可以使用無線網路 Local Bridge Mode 服
務。
學校需建置 RADIUS server 擔任認證服務,並自行定期維護允許使用之
MAC Address 清單(可參考附件自行架設)。
五、資訊安全之考量
當可以利用無線網路存取校內特定服務,便有可能為駭客提供另一攻擊之
路徑。故在申請本項服務前,請各校務必考慮開啟本項服務後對於校內資訊安全
之衝擊,並完成相關資訊安全防護建置(例如調整防火牆、訂定密碼管理規則、
學務系統使用 https 傳送及使用自然人憑證登入..)。
六、行動裝置連線設定
1. Local Bridge Mode 採用的認證及傳送規範與 SSID:tc-802.1x 相同,因此設定
時請參考 tc-802.1x 的設定方式設定(設定方法相同僅 SSID 不同)。
2. 因 Windows 系統未內建認證所需的 PEAP-GTC Plug-In 元件,若未安裝則需先
至 SSID: tc 登入畫面中下載並安裝。Windows EAP-GTC 元件目前提供
Windows XP、Windows Vista 、Windows 7/8(32/64 位元)等作業系統。
3. 大部分 Android 裝置及所有的 Apple iOS 裝置已內建認證所需的元件,不用額
外再安裝。
七、附件:Free RADIUS server 架設
Free RADIUS server 架設
一、本範例以 CentOS6 來示範安裝 FreeRADIUS,其他 OS 請自行參考調整。
#yum install freeradius*
安裝後設定檔預設會放在 /etc/raddb 之下
二、修改設定檔
1. 修改 clients.conf
#vi /etc/raddb/clients.conf
在檔案最後加入允許查詢的教網中心 controller IP
client 163.17.38.208 {
secret = wireless-ap
}
client 163.17.38.209 {
secret = wireless-ap
}
2. 修改 proxy.conf
#vi /etc/raddb/clients.conf
確認 DEFAULT 段內容為下
realm DEFAULT {
type = radius
authhost = LOCAL
accthost = LOCAL
}
3. 啟動 radiusd 並設為開機啟動
#service radiusd restart
#chkconfig radiusd on
三、本機防火牆及學校防火牆加入允許來源為教網中心 controller IP 查詢的規則
1. 本機:
#vi /etc/sysconfig/iptables
加入
-A INPUT -s 163.17.38.208 -p udp --dport 1812:1814 -j ACCEPT
-A INPUT -s 163.17.38.209 -p udp --dport 1812:1814 -j ACCEPT 重新啟動 iptables
#service iptables restart
2. 學校防火牆 下面以 FG400 示範。
2-1 自訂服務
2-2 自訂位址
2-3 外對內加入防火牆規則
四、加入允許之行動裝置 MAC Address
#vi /etc/raddb/users
請將收集到的 MAC Address 依下面格式加入 users 檔
00000000000A Auth-Type := Local, User-Password := "00000000000A"
00000000000B Auth-Type := Local, User-Password := "00000000000B"
00000000000C Auth-Type := Local, User-Password := "00000000000C"
修改內容後需重新啟動 radiusd
#service radiusd restart
五、測試
#radtest 00000000000A 00000000000A 00000000000A 00000000000A 00000000000A 00000000000A 127.0.0.1 0 testing123
Sending Access-Request of id 131 to 127.0.0.1 port 1812
User-Name = "00000000000A 00000000000A 00000000000A"
User-Password = "00000000000A 00000000000A 00000000000A"
NAS-IP-Address = 127.0.0.1
NAS-Port = 0
Message-Authenticator = 0x00000000000000000000000000000000
rad_recv: Access Access----Accept packet from host 127.0.0.1 port 1812, id=131, length=20
有回應 Access----Accept 就是沒問題了。
2014年7月4日 星期五
2014年6月10日 星期二
Free RADIUS server 架設
Free RADIUS server 架設
yum install freeradius* -y
/bin/cp /163.17.209.1/etc/raddb/clients.conf /etc/raddb/. -f
/bin/cp /163.17.209.1/etc/raddb/proxy.conf /etc/raddb/. -f
/bin/cp /163.17.209.1/etc/raddb/users /etc/raddb/. -f
service radiusd restart
radtest 00000000000A 00000000000A 127.0.0.1 0 testing123
一、本範例以 CentOS6 來示範安裝 FreeRADIUS,其他 OS 請自行參考調整。
#yum install freeradius*
安裝後設定檔預設會放在 /etc/raddb 之下
二、修改設定檔
1. 修改 clients.conf
#vi /etc/raddb/clients.conf
在檔案最後加入允許查詢的教網中心 controller IP
client 163.17.38.208 {
secret = wireless-ap
}
client 163.17.38.209 {
secret = wireless-ap
}
2. 修改 proxy.conf
#vi /etc/raddb/clients.conf
確認 DEFAULT 段內容為下
realm DEFAULT {
type = radius
authhost = LOCAL
accthost = LOCAL
}
3. 啟動 radiusd 並設為開機啟動
#service radiusd restart
#chkconfig radiusd on
三、本機防火牆及學校防火牆加入允許來源為教網中心 controller IP 查詢的規則
1. 本機:
#vi /etc/sysconfig/iptables
加入
-A INPUT -s 163.17.38.208 -p udp --dport 1812:1814 -j ACCEPT
-A INPUT -s 163.17.38.209 -p udp --dport 1812:1814 -j ACCEPT 重新啟動 iptables
#service iptables restart
2. 學校防火牆 下面以 FG400 示範。
2-1 自訂服務
2-2 自訂位址
2-3 外對內加入防火牆規則
四、加入允許之行動裝置 MAC Address
#vi /etc/raddb/users
請將收集到的 MAC Address 依下面格式加入 users 檔
00000000000A Auth-Type := Local, User-Password := "00000000000A"
00000000000B Auth-Type := Local, User-Password := "00000000000B"
00000000000C Auth-Type := Local, User-Password := "00000000000C"
修改內容後需重新啟動 radiusd
#service radiusd restart
五、測試
#radtest 00000000000A 00000000000A 00000000000A 00000000000A 00000000000A 00000000000A 127.0.0.1 0 testing123
Sending Access-Request of id 131 to 127.0.0.1 port 1812
User-Name = "00000000000A 00000000000A 00000000000A"
User-Password = "00000000000A 00000000000A 00000000000A"
NAS-IP-Address = 127.0.0.1
NAS-Port = 0
Message-Authenticator = 0x00000000000000000000000000000000
rad_recv: Access Access----Accept packet from host 127.0.0.1 port 1812, id=131, length=20
有回應 Access----Accept 就是沒問題了。
yum install freeradius* -y
/bin/cp /163.17.209.1/etc/raddb/clients.conf /etc/raddb/. -f
/bin/cp /163.17.209.1/etc/raddb/proxy.conf /etc/raddb/. -f
/bin/cp /163.17.209.1/etc/raddb/users /etc/raddb/. -f
service radiusd restart
radtest 00000000000A 00000000000A 127.0.0.1 0 testing123
一、本範例以 CentOS6 來示範安裝 FreeRADIUS,其他 OS 請自行參考調整。
#yum install freeradius*
安裝後設定檔預設會放在 /etc/raddb 之下
二、修改設定檔
1. 修改 clients.conf
#vi /etc/raddb/clients.conf
在檔案最後加入允許查詢的教網中心 controller IP
client 163.17.38.208 {
secret = wireless-ap
}
client 163.17.38.209 {
secret = wireless-ap
}
2. 修改 proxy.conf
#vi /etc/raddb/clients.conf
確認 DEFAULT 段內容為下
realm DEFAULT {
type = radius
authhost = LOCAL
accthost = LOCAL
}
3. 啟動 radiusd 並設為開機啟動
#service radiusd restart
#chkconfig radiusd on
三、本機防火牆及學校防火牆加入允許來源為教網中心 controller IP 查詢的規則
1. 本機:
#vi /etc/sysconfig/iptables
加入
-A INPUT -s 163.17.38.208 -p udp --dport 1812:1814 -j ACCEPT
-A INPUT -s 163.17.38.209 -p udp --dport 1812:1814 -j ACCEPT 重新啟動 iptables
#service iptables restart
2. 學校防火牆 下面以 FG400 示範。
2-1 自訂服務
2-2 自訂位址
2-3 外對內加入防火牆規則
四、加入允許之行動裝置 MAC Address
#vi /etc/raddb/users
請將收集到的 MAC Address 依下面格式加入 users 檔
00000000000A Auth-Type := Local, User-Password := "00000000000A"
00000000000B Auth-Type := Local, User-Password := "00000000000B"
00000000000C Auth-Type := Local, User-Password := "00000000000C"
修改內容後需重新啟動 radiusd
#service radiusd restart
五、測試
#radtest 00000000000A 00000000000A 00000000000A 00000000000A 00000000000A 00000000000A 127.0.0.1 0 testing123
Sending Access-Request of id 131 to 127.0.0.1 port 1812
User-Name = "00000000000A 00000000000A 00000000000A"
User-Password = "00000000000A 00000000000A 00000000000A"
NAS-IP-Address = 127.0.0.1
NAS-Port = 0
Message-Authenticator = 0x00000000000000000000000000000000
rad_recv: Access Access----Accept packet from host 127.0.0.1 port 1812, id=131, length=20
有回應 Access----Accept 就是沒問題了。
2014年4月29日 星期二
Step by Step Free Radius Configuration authenticated by LDAP
I am installing Free-Radius Server integrated with OpenLDAP
server on CentOS 5.5 using kernel 2.6.18-194.el5. I will install all packages
using yum configured on CentOS server.
You can configure OpenLDAP using my blog using Link http://jitendrakumaryogi.blogspot.in/2013/09/ldapsamba_23.html.
After Installing OpenLDAP you can configure Free-Radius Server.
I am checking the CentOS configuration on Server.
[root@ldapnoida ~]# cat /etc/redhat-release
CentOS
release 5.5 (Final)
[root@ldapnoida ~]# uname -a
Linux
ldapnoida.example.com 2.6.18-194.el5 #1 SMP Fri Apr 2 14:58:14 EDT 2010 x86_64
x86_64 x86_64 GNU/Linux
You can Install
FreeRadius packages on server using yum.
[root@ldapnoida ~]# yum install
freeradius*
It will
install following FreeRadius Packages on server.
[root@ldapnoida
~]# rpm -qa | grep radius
freeradius2-krb5-2.1.12-5.el5
freeradius2-postgresql-2.1.12-5.el5
freeradius2-utils-2.1.12-5.el5
freeradius2-python-2.1.12-5.el5
freeradius2-2.1.12-5.el5
freeradius2-ldap-2.1.12-5.el5
freeradius2-mysql-2.1.12-5.el5
freeradius2-unixODBC-2.1.12-5.el5
freeradius2-perl-2.1.12-5.el5
Once the installation is complete, “/etc/raddb”
directory is created which contains all configuration files of FreeRadius
server.
[root@ldapnoida raddb]# cd /etc/raddb/
[root@ldapnoida raddb]# vi eap.conf
default_eap_type
= md5
Now, open the file named “ldap” In “/etc/raddb/modules”
directory and change the configuration to the following:
[root@ldapnoida raddb]# cd modules/
[root@ldapnoida modules]# pwd
/etc/raddb/modules
[root@ldapnoida modules]# vi ldap
ldap {
#
#
Note that this needs to match the name in the LDAP
#
server certificate, if you're using ldaps.
server = "127.0.0.1" #
Local LDAP Server on same host
identity =
"cn=Manager,dc=example,dc=com" #ldap
Account to Manage LDAP server
password = root123 #
Password of above mentioned ldap account
basedn = "dc=example,dc=com"
filter =
"(uid=%{%{Stripped-User-Name}:-%{User-Name}})"
Now open
file “ /etc/raddb/sites-available/default” and change the following parameters
into authorize section in this file.
[root@ldapnoida sites-available]# vi
/etc/raddb/sites-available/default
authorize {
#
The ldap module will set Auth-Type to LDAP if it has not
#
already been set
ldap #Uncomment ldap
#
Read the 'users' file
#
files #Comment files
Now open
file “/etc/raddb/sites-available/inner-tunnel”
and change the following parameters into
authorize and authenticate section in this file.
[root@ldapnoida sites-available]# vi
/etc/raddb/sites-available/inner-tunnel
authorize {
#
Read the 'users' file
# files #Comment files
#
The ldap module will set Auth-Type to LDAP if it has not
#
already been set
ldap #Uncomment ldap
authenticate
{
# Uncomment it if you want to use
ldap for authentication
#
# Note that this means
"check plain-text password against
# the ldap database",
which means that EAP won't work,
# as it does not supply a plain-text
password.
Auth-Type LDAP {
ldap
}
Open the “clients.conf” file and edit the IP address at 34th line of file
i.e. ip address and enter the IP address of your radius server. Edit the client section to allow the APs (Access
Points) to communicate with your radius server.
Configuration would something look like this:
[root@ldapnoida raddb]# vi
client
10.226.0.0/16 {
secret = 1234 # Radius Secret
Key to give on Access Points
shortname = radping # It is User Defined name of
your choice
}
Run the radius server in debug mode with “radius
-X” and try to authenticate a user.
Testing of Radius Server
authenticated with LDAP Server.
My Radius
& Ldap Server IP Address is 10.226.2.66 which will be used for testing.
[root@ldapnoida
raddb]# ifconfig
eth0 Link encap:Ethernet HWaddr 00:50:56:90:01:0D
inet addr:10.226.2.66 Bcast:10.226.15.255 Mask:255.255.240.0
inet6 addr:
fe80::250:56ff:fe90:10d/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500
Metric:1
RX packets:65186388 errors:0
dropped:0 overruns:0 frame:0
TX packets:674273 errors:0 dropped:0
overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:9508735851 (8.8 GiB) TX bytes:113603579 (108.3 MiB)
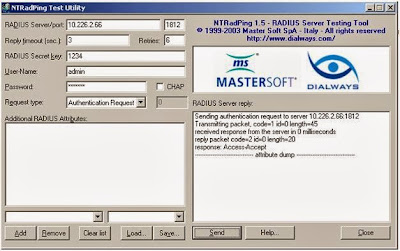
You can download
NTRadPing tool from Link http://www.novell.com/coolsolutions/tools/14377.html
and test the Radius user authentication using this tool.
As per
picture I authenticated admin user on ldap using radius and it is accepted and
access is given.
radiusd:
#### Opening IP addresses and Ports ####
listen {
type = "auth"
ipaddr = *
port = 0
}
listen {
type = "acct"
ipaddr = *
port = 0
}
listen {
type = "control"
listen {
socket =
"/var/run/radiusd/radiusd.sock"
}
}
listen {
type = "auth"
ipaddr = 127.0.0.1
port = 18120
}
... adding new socket proxy address * port
49997
Listening on
authentication address * port 1812
Listening on
accounting address * port 1813
Listening on
command file /var/run/radiusd/radiusd.sock
Listening on
authentication address 127.0.0.1 port 18120 as server inner-tunnel
Listening on
proxy address * port 1814
Ready to
process requests.
rad_recv:
Access-Request packet from host 10.226.1.206 port 37858, id=0, length=45
User-Name = "admin"
User-Password = "root123"
# Executing
section authorize from file /etc/raddb/sites-enabled/default
+- entering
group authorize {...}
++[preprocess]
returns ok
++[chap] returns
noop
++[mschap]
returns noop
++[digest]
returns noop
[suffix] No
'@' in User-Name = "admin", looking up realm NULL
[suffix] No
such realm "NULL"
++[suffix]
returns noop
[ntdomain]
No '\' in User-Name = "admin", looking up realm NULL
[ntdomain]
No such realm "NULL"
++[ntdomain]
returns noop
[eap] No
EAP-Message, not doing EAP
++[eap]
returns noop
[ldap]
performing user authorization for admin
[ldap] expand: %{Stripped-User-Name} ->
[ldap] ... expanding second conditional
[ldap] expand: %{User-Name} -> admin
[ldap] expand:
(uid=%{%{Stripped-User-Name}:-%{User-Name}}) -> (uid=admin)
[ldap] expand: dc=example,dc=com -> dc=example,dc=com
[ldap] ldap_get_conn: Checking Id: 0
[ldap] ldap_get_conn: Got Id: 0
[ldap] attempting LDAP reconnection
[ldap] (re)connect to 127.0.0.1:389,
authentication 0
[ldap] bind as cn=Manager,dc=example,dc=com/root123
to 127.0.0.1:389
[ldap] waiting for bind result ...
[ldap] Bind was successful
[ldap] performing search in dc=example,dc=com,
with filter (uid=admin)
[ldap]
looking for check items in directory...
[ldap] userPassword ->
Password-With-Header == "{crypt}x"
[ldap] sambaNtPassword -> NT-Password ==
0x3836313939443144384638323935373639354134304642453632443346443846
[ldap]
looking for reply items in directory...
[ldap] user
admin authorized to use remote access
[ldap] ldap_release_conn: Release Id: 0
++[ldap]
returns ok
++[expiration]
returns noop
++[logintime]
returns noop
[pap]
Normalizing NT-Password from hex encoding
++[pap]
returns updated
Found
Auth-Type = PAP
# Executing
group from file /etc/raddb/sites-enabled/default
+- entering
group PAP {...}
[pap] login attempt with password
"root123"
[pap] Using NT encryption.
[pap]
expand: %{User-Password} -> root123
[pap] NT-Hash of root123 =
86199d1d8f82957695a40fbe62d3fd8f
[pap]
expand: %{mschap:NT-Hash %{User-Password}} ->
86199d1d8f82957695a40fbe62d3fd8f
[pap] User authenticated successfully
++[pap]
returns ok
# Executing
section post-auth from file /etc/raddb/sites-enabled/default
+- entering
group post-auth {...}
++[exec]
returns noop
Sending
Access-Accept of id 0 to 10.226.1.206 port 37858
Finished
request 0.
Going to the
next request
Waking up in
4.9 seconds.
Cleaning up
request 0 ID 0 with timestamp +12
Ready to process
requests.
訂閱:
文章 (Atom)