I am installing Free-Radius Server integrated with OpenLDAP
server on CentOS 5.5 using kernel 2.6.18-194.el5. I will install all packages
using yum configured on CentOS server.
You can configure OpenLDAP using my blog using Link http://jitendrakumaryogi.blogspot.in/2013/09/ldapsamba_23.html.
After Installing OpenLDAP you can configure Free-Radius Server.
I am checking the CentOS configuration on Server.
[root@ldapnoida ~]# cat /etc/redhat-release
CentOS
release 5.5 (Final)
[root@ldapnoida ~]# uname -a
Linux
ldapnoida.example.com 2.6.18-194.el5 #1 SMP Fri Apr 2 14:58:14 EDT 2010 x86_64
x86_64 x86_64 GNU/Linux
You can Install
FreeRadius packages on server using yum.
[root@ldapnoida ~]# yum install
freeradius*
It will
install following FreeRadius Packages on server.
[root@ldapnoida
~]# rpm -qa | grep radius
freeradius2-krb5-2.1.12-5.el5
freeradius2-postgresql-2.1.12-5.el5
freeradius2-utils-2.1.12-5.el5
freeradius2-python-2.1.12-5.el5
freeradius2-2.1.12-5.el5
freeradius2-ldap-2.1.12-5.el5
freeradius2-mysql-2.1.12-5.el5
freeradius2-unixODBC-2.1.12-5.el5
freeradius2-perl-2.1.12-5.el5
Once the installation is complete, “/etc/raddb”
directory is created which contains all configuration files of FreeRadius
server.
[root@ldapnoida raddb]# cd /etc/raddb/
[root@ldapnoida raddb]# vi eap.conf
default_eap_type
= md5
Now, open the file named “ldap” In “/etc/raddb/modules”
directory and change the configuration to the following:
[root@ldapnoida raddb]# cd modules/
[root@ldapnoida modules]# pwd
/etc/raddb/modules
[root@ldapnoida modules]# vi ldap
ldap {
#
#
Note that this needs to match the name in the LDAP
#
server certificate, if you're using ldaps.
server = "127.0.0.1" #
Local LDAP Server on same host
identity =
"cn=Manager,dc=example,dc=com" #ldap
Account to Manage LDAP server
password = root123 #
Password of above mentioned ldap account
basedn = "dc=example,dc=com"
filter =
"(uid=%{%{Stripped-User-Name}:-%{User-Name}})"
Now open
file “ /etc/raddb/sites-available/default” and change the following parameters
into authorize section in this file.
[root@ldapnoida sites-available]# vi
/etc/raddb/sites-available/default
authorize {
#
The ldap module will set Auth-Type to LDAP if it has not
#
already been set
ldap #Uncomment ldap
#
Read the 'users' file
#
files #Comment files
Now open
file “/etc/raddb/sites-available/inner-tunnel”
and change the following parameters into
authorize and authenticate section in this file.
[root@ldapnoida sites-available]# vi
/etc/raddb/sites-available/inner-tunnel
authorize {
#
Read the 'users' file
# files #Comment files
#
The ldap module will set Auth-Type to LDAP if it has not
#
already been set
ldap #Uncomment ldap
authenticate
{
# Uncomment it if you want to use
ldap for authentication
#
# Note that this means
"check plain-text password against
# the ldap database",
which means that EAP won't work,
# as it does not supply a plain-text
password.
Auth-Type LDAP {
ldap
}
Open the “clients.conf” file and edit the IP address at 34th line of file
i.e. ip address and enter the IP address of your radius server. Edit the client section to allow the APs (Access
Points) to communicate with your radius server.
Configuration would something look like this:
[root@ldapnoida raddb]# vi
client
10.226.0.0/16 {
secret = 1234 # Radius Secret
Key to give on Access Points
shortname = radping # It is User Defined name of
your choice
}
Run the radius server in debug mode with “radius
-X” and try to authenticate a user.
Testing of Radius Server
authenticated with LDAP Server.
My Radius
& Ldap Server IP Address is 10.226.2.66 which will be used for testing.
[root@ldapnoida
raddb]# ifconfig
eth0 Link encap:Ethernet HWaddr 00:50:56:90:01:0D
inet addr:10.226.2.66 Bcast:10.226.15.255 Mask:255.255.240.0
inet6 addr:
fe80::250:56ff:fe90:10d/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500
Metric:1
RX packets:65186388 errors:0
dropped:0 overruns:0 frame:0
TX packets:674273 errors:0 dropped:0
overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:9508735851 (8.8 GiB) TX bytes:113603579 (108.3 MiB)
You can download
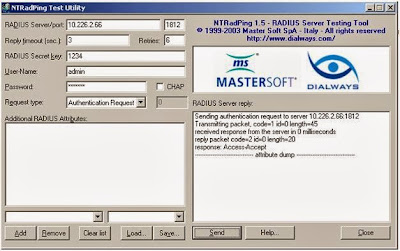
NTRadPing tool from Link http://www.novell.com/coolsolutions/tools/14377.html
and test the Radius user authentication using this tool.
As per
picture I authenticated admin user on ldap using radius and it is accepted and
access is given.
radiusd:
#### Opening IP addresses and Ports ####
listen {
type = "auth"
ipaddr = *
port = 0
}
listen {
type = "acct"
ipaddr = *
port = 0
}
listen {
type = "control"
listen {
socket =
"/var/run/radiusd/radiusd.sock"
}
}
listen {
type = "auth"
ipaddr = 127.0.0.1
port = 18120
}
... adding new socket proxy address * port
49997
Listening on
authentication address * port 1812
Listening on
accounting address * port 1813
Listening on
command file /var/run/radiusd/radiusd.sock
Listening on
authentication address 127.0.0.1 port 18120 as server inner-tunnel
Listening on
proxy address * port 1814
Ready to
process requests.
rad_recv:
Access-Request packet from host 10.226.1.206 port 37858, id=0, length=45
User-Name = "admin"
User-Password = "root123"
# Executing
section authorize from file /etc/raddb/sites-enabled/default
+- entering
group authorize {...}
++[preprocess]
returns ok
++[chap] returns
noop
++[mschap]
returns noop
++[digest]
returns noop
[suffix] No
'@' in User-Name = "admin", looking up realm NULL
[suffix] No
such realm "NULL"
++[suffix]
returns noop
[ntdomain]
No '\' in User-Name = "admin", looking up realm NULL
[ntdomain]
No such realm "NULL"
++[ntdomain]
returns noop
[eap] No
EAP-Message, not doing EAP
++[eap]
returns noop
[ldap]
performing user authorization for admin
[ldap] expand: %{Stripped-User-Name} ->
[ldap] ... expanding second conditional
[ldap] expand: %{User-Name} -> admin
[ldap] expand:
(uid=%{%{Stripped-User-Name}:-%{User-Name}}) -> (uid=admin)
[ldap] expand: dc=example,dc=com -> dc=example,dc=com
[ldap] ldap_get_conn: Checking Id: 0
[ldap] ldap_get_conn: Got Id: 0
[ldap] attempting LDAP reconnection
[ldap] (re)connect to 127.0.0.1:389,
authentication 0
[ldap] bind as cn=Manager,dc=example,dc=com/root123
to 127.0.0.1:389
[ldap] waiting for bind result ...
[ldap] Bind was successful
[ldap] performing search in dc=example,dc=com,
with filter (uid=admin)
[ldap]
looking for check items in directory...
[ldap] userPassword ->
Password-With-Header == "{crypt}x"
[ldap] sambaNtPassword -> NT-Password ==
0x3836313939443144384638323935373639354134304642453632443346443846
[ldap]
looking for reply items in directory...
[ldap] user
admin authorized to use remote access
[ldap] ldap_release_conn: Release Id: 0
++[ldap]
returns ok
++[expiration]
returns noop
++[logintime]
returns noop
[pap]
Normalizing NT-Password from hex encoding
++[pap]
returns updated
Found
Auth-Type = PAP
# Executing
group from file /etc/raddb/sites-enabled/default
+- entering
group PAP {...}
[pap] login attempt with password
"root123"
[pap] Using NT encryption.
[pap]
expand: %{User-Password} -> root123
[pap] NT-Hash of root123 =
86199d1d8f82957695a40fbe62d3fd8f
[pap]
expand: %{mschap:NT-Hash %{User-Password}} ->
86199d1d8f82957695a40fbe62d3fd8f
[pap] User authenticated successfully
++[pap]
returns ok
# Executing
section post-auth from file /etc/raddb/sites-enabled/default
+- entering
group post-auth {...}
++[exec]
returns noop
Sending
Access-Accept of id 0 to 10.226.1.206 port 37858
Finished
request 0.
Going to the
next request
Waking up in
4.9 seconds.
Cleaning up
request 0 ID 0 with timestamp +12
Ready to process
requests.
沒有留言:
張貼留言